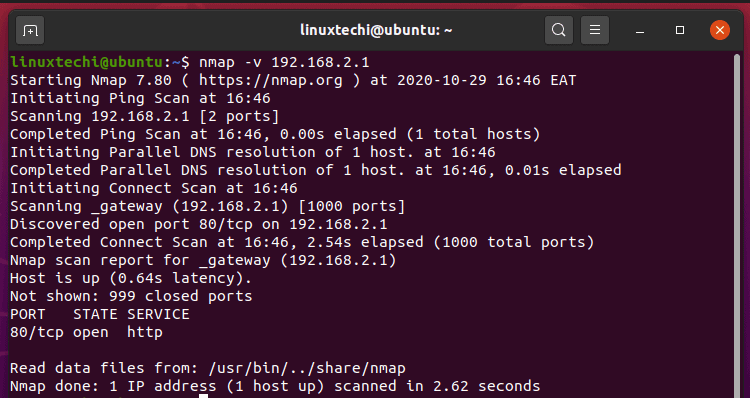
Nmap Policy. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. A default scan ( nmap <hostname>) of a host on my local network takes a fifth of a second. Next Timing and Performance One of my highest Nmap development priorities has always been performance. When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP. That is barely enough time to blink, but adds up when you are scanning hundreds or thousands of hosts. Reduce your risk by reading this legal guide before launching Nmap. Unless you use the -sT -Pn options, RAS connections (such as PPP dialups) and certain VPN clients are not supported.

Nmap Policy. That is barely enough time to blink, but adds up when you are scanning hundreds or thousands of hosts. A default scan ( nmap <hostname>) of a host on my local network takes a fifth of a second. Looking for online definition of NMAP or what NMAP stands for? Download the Free Nmap Security Scanner for Linux/Mac/Windows Downloading Nmap macOS Linux (RPM) Any other OS (source code) Older versions (and sometimes newer test releases) are available from the Nmap release archive (and really old ones are in dist-old ). Nmap is short for Network Mapper. Nmap Policy.
Apple Tree Dental, a healthcare nonprofit dedicated to oral health equity, is on a mission to remove barriers to oral health including transforming health care policy.
Like all security tools it can be used defensively, by a network manager, to identify weaknesses that need to.
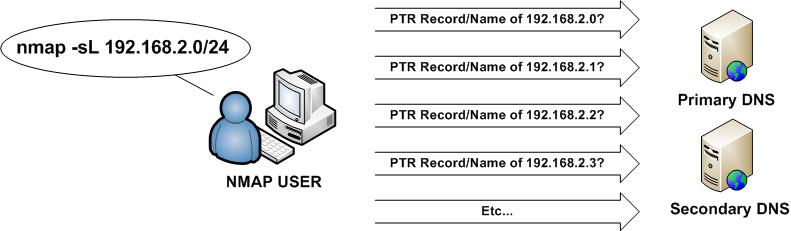
Nmap Policy. Note: Hostnames are queried against DNS, while IPs undergo a reverse-lookup. PolicyMap makes it possible for their team to better identify disparities and present necessary data for legislative change. Nmap is now one of the core tools used by network administrators to map their networks. That is barely enough time to blink, but adds up when you are scanning hundreds or thousands of hosts. Unless you use the -sT -Pn options, RAS connections (such as PPP dialups) and certain VPN clients are not supported.
Nmap Policy.